1. What Happened
In the past 30 days, SPI Logistics experienced two significant cargo theft incidents. In both cases, agents dispatched loads after receiving instructions from phone numbers that were not authorized or verified. The fraudulent parties had compromised the email accounts of legitimate carriers, allowing them to convincingly impersonate authorized personnel and intercept critical shipment information. As a result, valuable cargo was handed over to criminals, leading to substantial financial losses for SPI.
2. How It Happened
The thefts were orchestrated using a combination of email compromise and phone fraud:
- Email Compromise: The perpetrators gained unauthorized access to the email accounts of legitimate carriers, often through phishing schemes or credential theft. Once inside, they monitored communications and intercepted rate confirmations and shipment details.
- Impersonation via Phone: Using information obtained from compromised emails, the criminals contacted SPI agents from unauthorized phone numbers, posing as legitimate carrier representatives. The agents, trusting the apparent legitimacy of the requests, dispatched the loads based on these fraudulent instructions.
- Lack of Verification: A critical step was missed-verifying the phone numbers through a platform like Highway. Had the agents cross-checked the numbers, they would have discovered that the calls were not coming from authorized contacts, potentially preventing the theft.
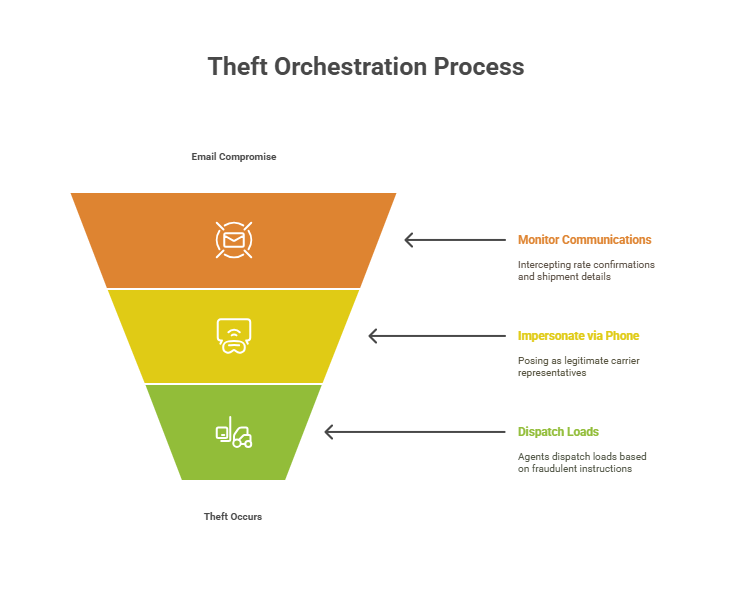
These incidents are part of a broader trend in the logistics industry, where sophisticated fraudsters exploit weak points in verification processes, often using AI-driven phishing, spoofed credentials, and burner phones to bypass traditional security checks.
3. What Could Have Been Done to Prevent It
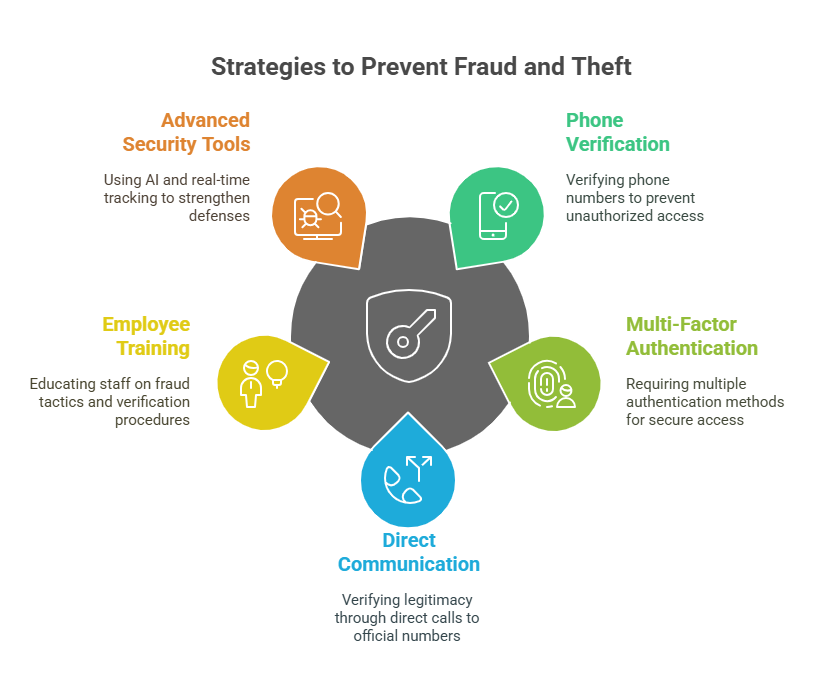
Several preventative measures could have mitigated or entirely avoided these incidents:
- Strict Phone Number Verification: Implementing mandatory verification of all phone numbers through trusted platforms (such as Highway) would have immediately flagged the unauthorized numbers and stopped the fraud in its tracks.
- Multi-Factor Authentication (MFA): Requiring MFA for access to carrier email accounts would reduce the risk of email compromise.
- Direct Communication Protocols: Encouraging agents to verify carrier legitimacy by making direct calls to numbers listed in official databases (e.g., FMCSA, SAFER) instead of relying solely on incoming communications.
- Employee Training: Regular training on the latest fraud tactics and the importance of following verification procedures can help staff recognize red flags and avoid social engineering traps.
- Use of Advanced Security Tools: Employing AI-driven monitoring, real-time shipment tracking, and document authentication can further strengthen defenses against evolving cargo theft tactics.
4. How SPI Solved the Problem
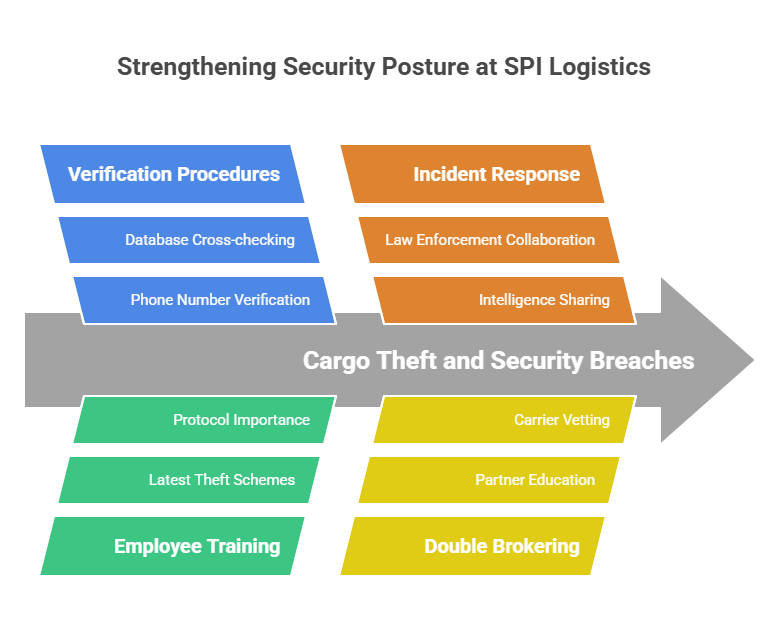
In response to these incidents, SPI Logistics took decisive steps to strengthen its security posture:
- Reinforced Verification Procedures: SPI mandated strict adherence to phone number verification for all load dispatches, making it a non-negotiable part of their workflow. Agents are now required to cross-check all contact information using Highway or similar trusted databases before proceeding with any shipment instructions.
- Enhanced Employee Training: SPI launched updated training sessions focused on the latest cargo theft schemes, emphasizing the critical nature of every step in their security protocols and the severe consequences of skipping even one.
- Incident Response and Collaboration: SPI worked closely with law enforcement and industry partners to investigate the thefts, share intelligence on the tactics used, and recover stolen assets where possible.
- Continuous Monitoring and Review: The Company implemented regular audits of its verification processes and communication channels, ensuring compliance and identifying any emerging vulnerabilities.
- Crackdown on Double Brokering: SPI reinforced its stance against double brokering by educating partners on the risks, tightening carrier vetting protocols, and promoting industry awareness through resources like this guide on protecting your reputation as a freight broker.
These actions not only addressed the immediate aftermath of the thefts but also positioned SPI to better defend against increasingly sophisticated fraud and cargo theft schemes in the future.
Key Lesson:
Strict adherence to verification procedures-especially phone number verification-remains the most effective defense against modern cargo theft. Even a single skipped step can result in significant financial and reputational damage. Ongoing vigilance, employee education, and the use of advanced security tools are essential to safeguarding logistics operations in an era of rapidly evolving threats.




