Freight brokerages run on data. Every shipment tender, carrier onboarding packet, rate confirmation, invoice, and payment contains sensitive operational and financial information. As brokers digitize their workflows, cybersecurity is no longer an IT topic. It is a business survival requirement.
Selecting secure platforms requires more than trusting a vendor’s marketing. Brokers must understand how to evaluate software security for brokers, build a thorough cybersecurity checklist for brokers, and prioritize advanced protection features across TMS, CRM, accounting systems, and other operational tools.
This guide provides a comprehensive framework to help you choose resilient, compliant, and truly secure brokerage software.
Understanding the Cybersecurity Risks for Brokerages
Freight brokerages operate at the intersection of logistics coordination, financial transactions, carrier management, and client communication. This unique position exposes brokers to a wide range of cyber threats that are more targeted and sophisticated than many other industries experience (FreightWaves, n.d.). Every digital interaction, whether inside a TMS, CRM, accounting system, email platform, or load board, becomes a potential entry point for attackers.
For brokers, cybersecurity is not just about protecting data. It is about protecting revenue streams, shipper trust, carrier relationships, and regulatory compliance. A brokerage without strong digital defenses can face operational shutdown, financial loss, legal exposure, and long-term brand damage.
Before selecting software, it is essential to understand the risks. Brokers handle confidential shipment details, payment information, and personal client data. A single breach can damage reputation, result in financial losses, and create legal liabilities.
Key Risks Include:
1. Data Theft & Ransomware
Hackers target broker systems to steal shipment data and financial records or lock platforms for ransom.
Main Risks
- TMS shutdown and operational delays
- Stolen carrier banking info
- Leaked customer pricing
2. Unauthorized System Access
Weak passwords and lack of authentication allow hackers into TMS and CRM platforms.
What Happens
- Shipment data exposure
- Carrier database theft
- Manipulated load records (DAT Solutions, n.d.)
3. Insider Threats
Employees with unrestricted access can misuse or leak sensitive brokerage data.
Risks
- Exporting shipper or carrier lists
- Unauthorized data sharing
- Financial tampering
4. Compliance Failures
Using tools without proper security certifications can expose brokers to legal and financial penalties.
Risks
- Non-compliant CRMs or accounting systems
- Poor data handling practices
Steps to Mitigate Risks:
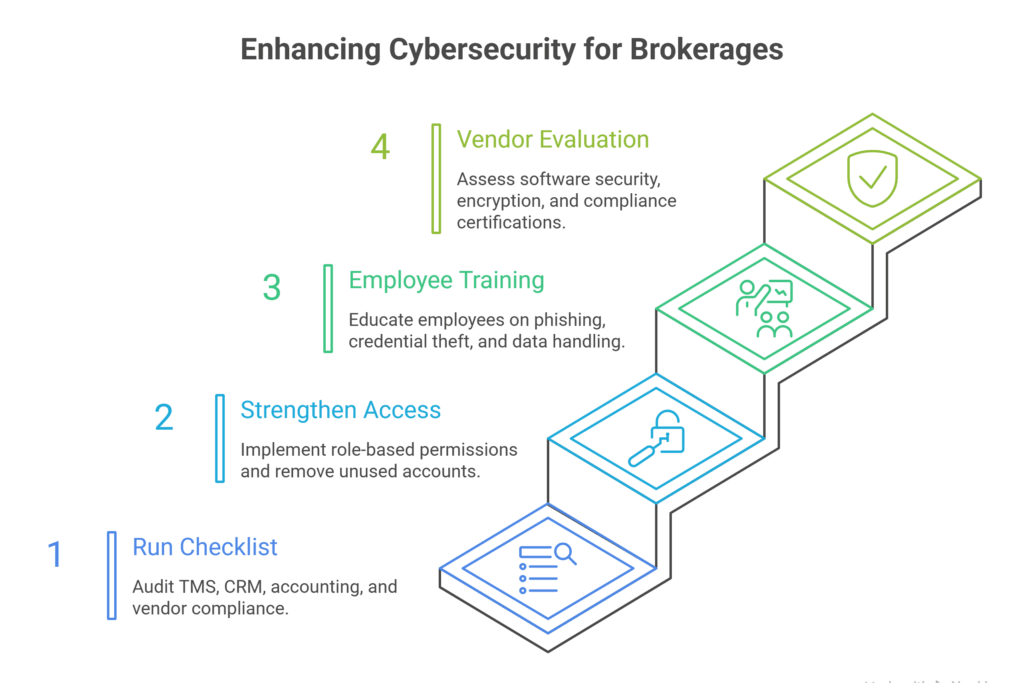
1. Run a Cybersecurity Checklist for Brokers
- Audit TMS security
- Review CRM access
- Verify accounting protections
- Evaluate vendor compliance
2. Strengthen Access Controls Across All Systems
- Role-based permissions
- Remove unused accounts
- Restrict sensitive data visibility
3. Employee Cybersecurity Training
- Recognize phishing emails
- Prevent credential theft
- Follow secure data handling protocols
4. Vendor Security Evaluation
- Understand how to evaluate software security for brokers
- Request encryption proof
- Confirm compliance certifications
“Brokers often overlook internal threats, but secure user management and continuous monitoring can prevent most breaches before they occur.”
Looking to safeguard your brokerage operations? Discover our Compliance & Risk Management solutions.
Security Features in TMS Software
A Transportation Management System (TMS) is the backbone of logistics operations. Ensuring your TMS has robust security features is essential for protecting shipment and client data (uShip, n.d.).
Critical Security Features to Look For:
- Data encryption in TMS and CRM to secure data both at rest and in transit
- Role-based access controls to limit who can view or modify sensitive shipment details
- Regular software updates and patches to address vulnerabilities
- Comprehensive audit logs for tracking system activity
- Two-factor authentication for user accounts
Checklist for Evaluating TMS Security:
1. Review Security Features in TMS Software With Vendors
Do not rely on marketing pages alone. Ask vendors to walk you through their actual protection mechanisms.
What to Look For During a Demo
- Role-based user permissions
- Login tracking and audit logs
- Data encryption in TMS and CRM integrations
- Secure document storage
- API protection for load board connections (uShip, n.d.)
This step is critical when choosing a secure TMS software because many platforms appear strong but lack real operational safeguards.
2. Request SOC 2 Compliance or Proof of Internal Security Controls
SOC 2 certification shows that the vendor follows strict data protection standards.
Why It Matters for Brokers
- Confirms secure handling of shipper and carrier data
- Demonstrates controlled internal access
- Reduces liability risks
If SOC 2 is unavailable, ask for:
- Security audit reports
- Data protection policies
- Breach response procedures
This supports your broader goal of data security in logistics management software.
3. Verify Backup and Disaster Recovery Capabilities
Your brokerage must continue operating even if systems fail.
Questions to Ask
- How often is data backed up?
- Are backups encrypted?
- How quickly can systems be restored?
- Is there redundancy across servers?
Lack of recovery planning is one of the most overlooked risks in digital tools for brokerage security.
4. Ensure GDPR Compliance for European Shipments
If your brokerage touches EU-related data, GDPR compliance in brokerage tools is mandatory.
Your TMS Must Support
- Secure storage of personal data
- Data access and deletion rights
- Encrypted communication channels
- Documented privacy controls
This ties directly into data security in logistics management software and protects your brokerage from legal penalties.
“When choosing a secure TMS software, brokers must prioritize encryption, access control, and compliance certifications over convenience features.”
Which TMS security feature do you consider most crucial for protecting your brokerage’s sensitive shipment data?
CRM Data Security Best Practices
Customer Relationship Management (CRM) systems store sensitive client and partner data. A breach can lead to lost contracts, reputational damage, and legal exposure (FreightWaves, n.d.).
Essential CRM Security Measures:
- CRM data security best practices include using strong passwords, enforcing two-factor authentication in CRMs, and restricting access to only necessary personnel (IBM, n.d.)
- Data encryption in TMS and CRM to prevent interception of emails, documents, and call recordings
- Regular security audits to identify vulnerabilities
- Integration with secure email and document sharing platforms
- Role-based permissions and automatic session timeouts
Steps to Evaluate CRM Security:
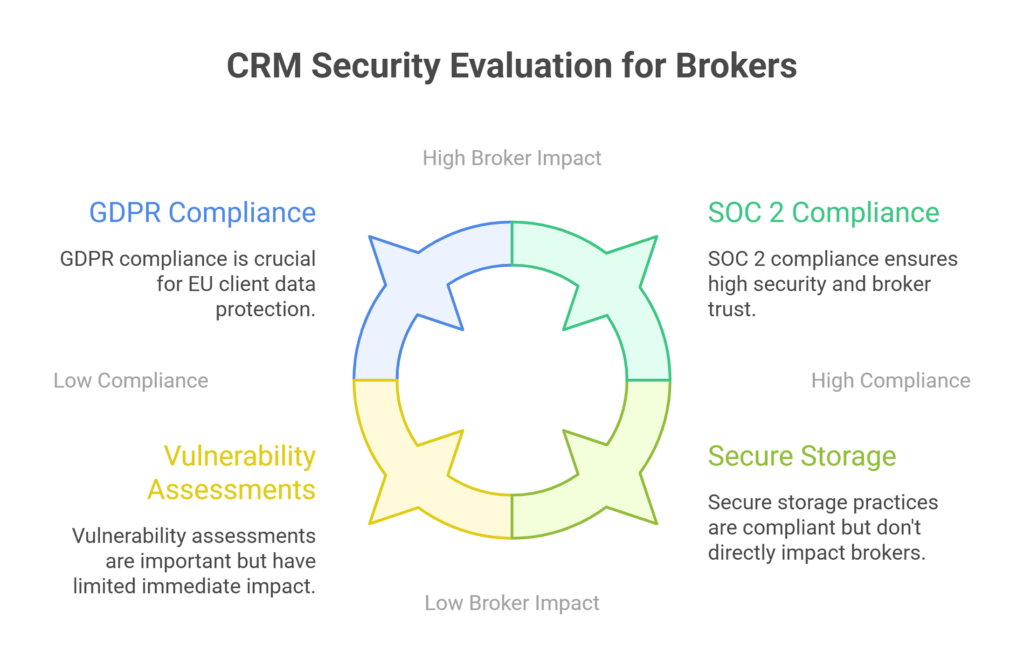
1. Review Vendor Compliance With SOC 2 Compliance for CRMs
SOC 2 compliance for CRMs demonstrates that the vendor follows strict standards for data security, confidentiality, and system integrity.
Why It Matters for Brokers
- Protects shipper and partner contact data
- Ensures controlled internal access by the CRM provider
- Confirms monitoring and risk management processes
- Reduces legal and reputational exposure
2. Ask About GDPR Compliance in Data Storage and Transfer Protocols
If your brokerage communicates with or stores data from EU-based clients, GDPR compliance in brokerage tools is mandatory (IBM, n.d.).
CRM Must Support
- Secure storage of personal information
- Data encryption in TMS and CRM integrations
- Consent tracking and deletion requests
- Transparent data processing policies
3. Check for Vulnerability Assessments and Penetration Testing Reports
Regular testing shows that the vendor actively searches for weaknesses before attackers find them.
Why Brokers Should Care
- Identifies security gaps early
- Prevents unauthorized system access
- Protects sensitive brokerage communication
- Ensures ongoing CRM data security best practices
“Many brokers underestimate CRM vulnerabilities. Encrypting data and implementing two-factor authentication can prevent the majority of unauthorized access incidents.”
How does your brokerage ensure client data remains secure within your CRM?
Accounting Software Cybersecurity Features
Financial data is a prime target for cybercriminals. Brokers must carefully evaluate accounting software cybersecurity features before adoption.
Security Features to Prioritize:
- Strong data encryption in TMS and CRM and secure connections for financial transactions (FreightWaves, n.d.)
- Multi-factor authentication for all accounting access
- Automated audit trails for compliance reporting
- Backup systems to prevent data loss
- Integration with secure financial software for brokerages
Steps to Ensure Safe Accounting Software:
1. Confirm the Software Provides Secure Accounting Systems for Brokers
Not all accounting tools are designed for the brokerage environment. Your platform must actively protect financial and payment data.
What to Verify
- Role-based financial access
- Encrypted payment and banking data
- Approval workflows before releasing payments
- Audit logs tracking edits and transactions
Strong secure accounting systems for brokers reduce fraud, internal misuse, and external attacks.
2. Ensure Compliance With GDPR and Local Data Regulations
Brokerages handling international clients must use accounting software that aligns with privacy and data protection laws.
Why It Matters
- Protects personal financial data
- Prevents regulatory penalties
- Builds trust with shippers and carriers
Look for clear data handling policies and confirmation that the platform supports GDPR or equivalent standards.
3. Evaluate Frequency of Security Updates and Patches
Outdated accounting software is a major vulnerability.
Key Questions
- How often are updates released?
- Are patches automatic?
- How quickly are security threats addressed?
Regular updates ensure your system remains protected from newly discovered threats and exploits.
“Selecting accounting software without robust cybersecurity is a risk you cannot afford. The right system combines encryption, multi-factor authentication, and continuous monitoring.”
Which accounting software security feature would give you the most confidence in handling sensitive financial data?
Evaluating Other Digital Tools for Brokerage Security
Beyond TMS, CRM, and accounting software, brokers rely on various tools such as document management systems, communication platforms, and analytics software. Ensuring all these tools meet security standards is vital (FreightWaves, n.d.).
Key Considerations:
- Confirm integration with existing systems without compromising security
- Require vendors to provide clear data handling policies and compliance certifications
- Use a cybersecurity checklist for brokers to audit all digital tools
- Prioritize tools with secure cloud hosting and encrypted connections
- Evaluate vendor reputation and history of security incidents
Steps to Evaluate Software Security for Brokers:
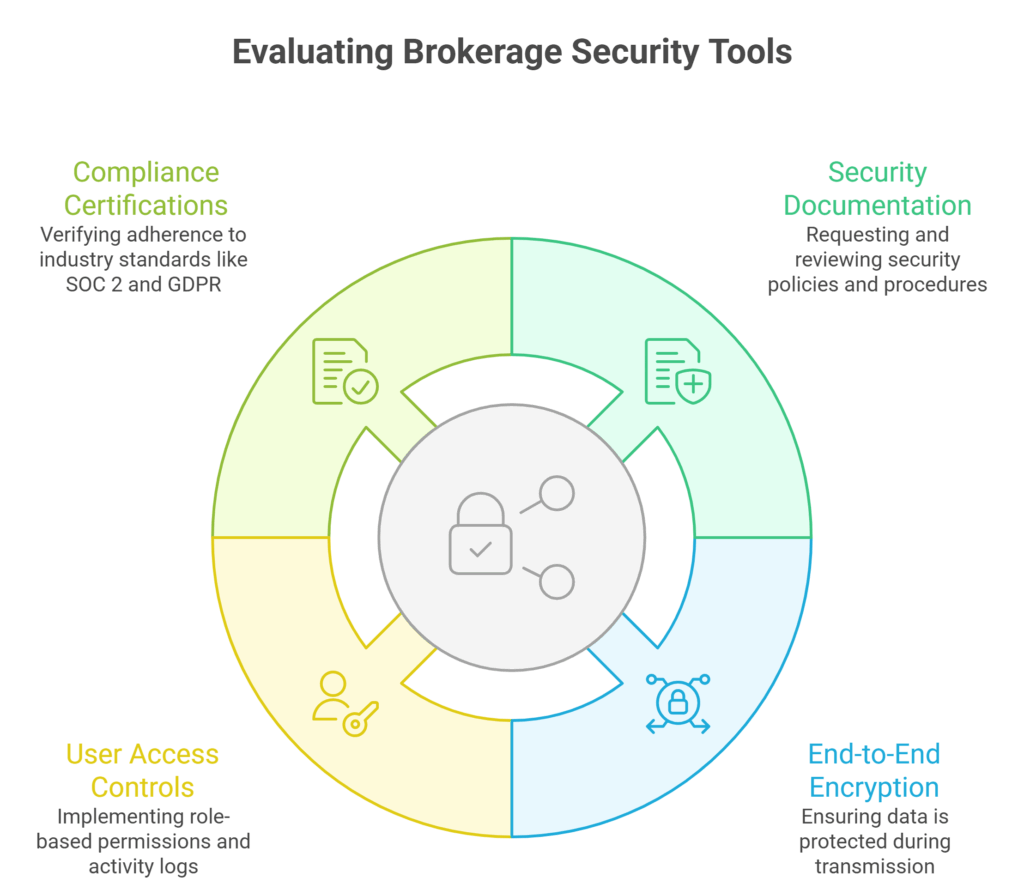
1. Request Security Documentation and Perform Vendor Due Diligence
Never assume a platform is secure. Ask vendors to provide clear proof of their internal security practices (uShip, n.d.).
What to Request
- Security and privacy policies
- Data protection procedures
- Breach response plan
- Hosting and infrastructure details
- Third-party security certifications
This step helps brokers filter out risky providers before exposing operational or financial data.
2. Check for Digital Tools for Brokerage Security With End-to-End Encryption
Encryption ensures data cannot be intercepted or read during transmission.
Why It Matters
- Protects shipper and carrier communications
- Secures financial data transfers
- Prevents exposure during system integrations
- Strengthens digital tools for brokerage security
Look for platforms that encrypt data both at rest and in transit.
3. Review User Access Controls and System Logging
Software must allow brokers to control who can see, edit, or export data.
Key Features to Verify
- Role-based permissions
- Login tracking
- Activity logs
- Restrictions on downloads and exports
These controls prevent both external breaches and insider misuse.
4. Ensure Compliance With SOC 2, GDPR, and Financial Regulations
Compliance proves that a platform meets recognized security standards.
Why Brokers Should Prioritize This
- Protects customer and partner data
- Reduces liability exposure
- Supports enterprise shipper requirements
- Ensures legal operation across regions
Always confirm compliance certifications before trusting vendors with brokerage information.
“Even smaller digital tools can create vulnerabilities if they are not properly vetted. A comprehensive security review of all brokerage software is essential.”
Want to take your brokerage to the next level with secure, smart technology? See how our Freight Broker Technology can streamline your operations.
Frequently Asked Questions (FAQs)
1. What is the most important security feature in a TMS for brokers?
Data encryption, role-based access control, and audit logging are critical. These ensure shipment data cannot be accessed or altered by unauthorized users.
2. How can I evaluate software security for brokers before purchase?
Request vendor compliance certifications, conduct a cybersecurity checklist for brokers, and ask for detailed documentation on encryption, access controls, and audit logs.
3. Are CRM systems inherently secure for brokerage data?
Not all CRMs are secure by default. Implementing CRM data security best practices and selecting software with SOC 2 compliance and encryption ensures safety.
Secure Your Digital Freight Operations
Securing your brokerage’s digital ecosystem requires careful evaluation of TMS, CRM, accounting software, and other tools. By following a cybersecurity checklist for brokers and understanding how to evaluate software security for brokers, you can protect sensitive shipment, client, and financial data. Prioritize encryption, access control, compliance, and multi-factor authentication across all platforms. Regular audits and employee training will further strengthen your brokerage’s cybersecurity posture.
Ready to safeguard your brokerage and keep your data, and your business protected? Contact us to implement a comprehensive cybersecurity strategy.
References
FreightWaves. (n.d.). How brokers can protect data and prevent fraud. Retrieved from https://www.freightwaves.com
DAT Solutions. (n.d.). Cybersecurity best practices for freight brokers. Retrieved from https://www.dat.com
uShip. (n.d.). Understanding digital security in logistics operations. Retrieved from https://www.uship.com
IBM. (n.d.). Evaluating software security for businesses. Retrieved from https://www.ibm.com/security




